
Trust goes both ways
When you ask your customers to verify themselves, you’re asking them to trust you with their most precious asset: their identity. Prove yourself worthy of that trust—with the identity verification platform designed and certified to keep customer data safe. Because personal data is just that: personal.
Safeguarding your customer’s data: Security
We apply best-in-class security tools and practices to keep your customer data safe, every step of the way. Our security systems are designed to meet or exceed industry standards. All data served over our REST APIs secured using TLS 1.2 and https with OAuth where appropriate. IDVerse is also ISO security standard certified and conducts annual SOC 2 Type II audits.
End-to-end encryption: IDVerse uses end-to-end encryption of data both in transit and at rest, applying AES 256+ encryption.
Penetration Testing: We perform penetration tests at least 4 times per year, or after any significant upgrade/release. Development, testing and production environments are segregated. Each enterprise client is provided with a staging and production dedicated virtual private cloud.
Threat Management: We leverage market leading automated security tools across all our environments to stop threats efficiently and effectively. Our tools use a wide range of advanced threat defense techniques, including behavioural analysis, machine learning, and other forms of artificial intelligence.
Access Management: We apply best practice for access control, using the principle of least privilege or need to know basis, that is controlled through role based access, i.e. an individual only has the minimum access privileges necessary to perform a specific job or task and nothing more.

Data protection you can trust and tailor: Data Storage & Sovereignty
All customer data belongs to, and is controlled by you. IDVerse provides a full audit trail of each transaction (that includes both extracted data, turnaround times and geolocation data) that is either passed back to you via API or available in our Customer Portal. There are two options for storing your customer data, they are: On-premise (Turkey only), Cloud Single-Tenant, and Cloud Multi-Tenant.
- On-premise: All customer data is stored in your own dedicated on-site computers – Turkey only as required by regulation.
- Cloud Single-Tenant: All customer data is stored in a dedicated AWS Virtual Private Cloud (VPC). We will keep that data within the geographical region that you select it to be stored.
- Cloud Multi-Tenant: All customer data is stored in a shared AWS Virtual Private Cloud (VPC). We will keep that data within the geographical region that you select it to be stored.
Many governments and businesses now require that all customer data processed and stored in an IT system must remain within your country’s borders. IDVerse protects your customer data by keeping it within the country’s borders and preventing any cross border flow of that customer data.
- Australia: We use the AWS AsiaPac (Sydney) region, meaning no data is transferred outside of Australia, including backups.
- New Zealand: We use the AWS AsiaPac (Sydney) region, as there is no AWS instance currently within New Zealand. Noting, AWS has proposed for a New Zealand dedicated region in 2024 that we will leverage for our New Zealand clients.
- Turkey: All data is installed and runs on the servers on-premise of the business using IDVerse, rather than at a remote facility.
- United Kingdom: We use the AWS Europe (London) region, meaning no data is transferred outside of the United Kingdom, including backups.
- United States: We use the AWS US West (Oregon) region, meaning no data is transferred outside of America, including backups.
A resilient, highly reliable network: Availability
We’ve engineered our systems for highly availability and self redundancy so they can withstand the failure of an individual component or multiple components, such as servers and databases.
Availability: IDVerse has engineered its systems for highly available and self redundancy so it can withstand the failure of an individual component or multiple components, such as servers and databases.
DDoS: We have protections in place for Distributed Denial of Service (DDoS) attacks. This includes always-on detection and automatic inline mitigations that minimise application downtime and latency.
Load Management: We have auto-scaling and elastic load balancing to automatically distribute incoming application traffic across multiple instances and multiple availability zones to maintain steady, predictable performance.


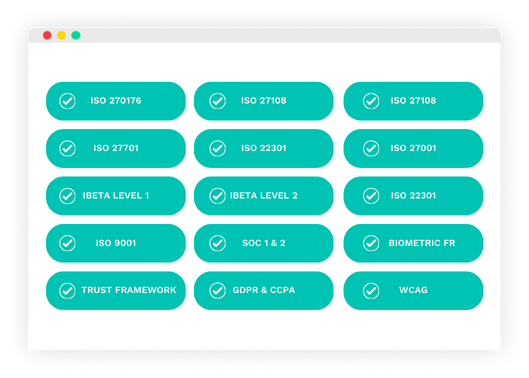
Equipped for the toughest standards: Compliance & Certifications
Our customers and regulators expect independent verification of our security, privacy, and compliance controls. In order to provide this, we undergo several independent third-party audits on a regular basis. Our platform meets the most stringent privacy, security and integrity standards – including iBeta, TDIF, SOC 2 and ISO 27001.
- The first and only commercial entity to be accredited under the Australian Government’s Trusted Digital Identity Framework (TDIF). We are an accredited Identity Service Provider (Identity Proofing Level IP1+, IP2).
- ISO 27001 is one of the most widely recognised and accepted independent security standards.
- ISO 27017 is a security standard specifically tailored for cloud service providers.
- ISO 27018 is a code of practice regarding the protection of personally identifiable information (PII) in the cloud.
- ISO 27701 is a privacy extension to ISO 27001 defining how organisations manage personal information to demonstrate compliance with privacy regulations around the world.
- ISO 29100 is a security extension to ensure there is an appropriate privacy framework in operation.
- ISO 22301 Business continuity management systems to ensure the security and resilience of our platform.
- ISO 30107-3 Biometric presentation attack detection with 100% success at Level 1 and Level 2.
- ISO 9001 demonstrates our ability to consistently provide products and services that meet client and regulatory requirements.
- SOC (Service Organisation Controls) audit framework relies on its Trust Principles and Criteria for security, availability, processing integrity, and confidentiality; Type 1 and 2 certified.
- Conformance to WCAG 2.0 Level AA which is essential for creating inclusive digital products.
- Biometric matching algorithm tested by a qualified third-party testing entity described in ISO 19795.
- Privacy independent compliance assessment.

